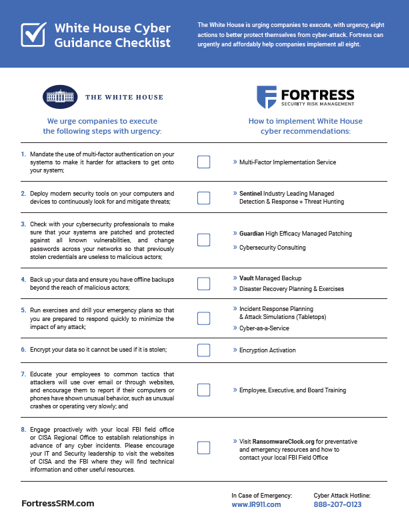
How to implement White House cyber recommendations:
»
Multi-Factor Implementation Service
» Sentinel Industry Leading Managed
Detection & Response + Threat Hunting
» Guardian High Efficacy Managed Patching
» Cybersecurity Consulting
» Cybersecurity Consulting
» Vault Managed Backup
» Disaster Recovery Planning & Exercises
» Disaster Recovery Planning & Exercises
» Incident Response Planning
& Attack Simulations (Tabletops)
» Cybersecurity-as-a-Service
» Cybersecurity-as-a-Service
» Encryption Activation
» Employee, Executive, and Board Training
» Visit RansomwareClock.org for preventative and emergency resources and how to contact your local FBI Field Office

We urge companies to execute the following steps with urgency:
1. Mandate the use of multi-factor authentication on your systems to make it harder for attackers to get onto your system;
2. Deploy modern security tools on your computers and devices to continuously look for and mitigate threats;
3. Check with your cybersecurity professionals to make sure that your systems are patched and protected against all known vulnerabilities, and change passwords across your networks so that previously stolen credentials are useless to malicious actors;
4. Back up your data and ensure you have offline backups beyond the reach of malicious actors;
5. Run exercises and drill your emergency plans so that you are prepared to respond quickly to minimize the impact of any attack;
6. Encrypt your data so it cannot be used if it is stolen;
7. Educate your employees to common tactics that attackers will use over email or through websites, and encourage them to report if their computers or phones have shown unusual behavior, such as unusual crashes or operating very slowly; and
8. Engage proactively with your local FBI field office or CISA Regional Office to establish relationships in advance of any cyber incidents. Please encourage your IT and Security leadership to visit the websites of CISA and the FBI where they will find technical information and other useful resources.
Download the White House Cyber Guidance Checklist
If you need help implementing these 8 actions to better protect your organization from cyber-attacks, Fortress can help. We also offer:
- Cybersecurity Assessments: Measured against best practice cybersecurity frameworks: ISO27001, NIST, or one based on your industry or company preference.
- Security Plan Development: We’ll develop a cybersecurity protection plan and “run-book” that identifies the scope, steps, processes, and resources required to properly react to a security breach.
- Cyber Tracking Software: Your requirements for compliance and the governance of risk and security management are handled using best-in-class security software.
- Cyber-Attack Simulations: Called Table-Top Exercises, these simulations bring together your Incident Response Team to identify gaps in response, practice technical and managerial responses, and review the coordination and communication structure and content.
Learn more about Fortress
Fortress Security Risk Management protects companies from the financial, operational, and emotional ravages of cybercrime by enhancing the performance of their people, processes, and technology.